Twitter was thrown into chaos on Wednesday after accounts for some of the world’s most recognizable public figures, executives and celebrities starting tweeting out links to bitcoin scams. Twitter says the attack happened because someone tricked or coerced an employee into providing access to internal Twitter administrative tools. This post is an attempt to lay out some of the timeline of the attack, and point to clues about who may have been behind it.
周三,世界上一些知名的公众人物、高管和名人的账户开始在推特上发布比特币骗局的链接,Twitter 陷入了混乱之中。推特表示,此次攻击是因为有人诱骗或胁迫一名员工访问推特内部管理工具。这篇帖子试图列出袭击的一些时间线,并指出幕后黑手的线索。
The first public signs of the intrusion came around 3 PM EDT, when the Twitter account for the cryptocurrency exchange Binance tweeted a message saying it had partnered with “CryptoForHealth” to give back 5000 bitcoin to the community, with a link where people could donate or send money.
入侵的第一个公开迹象出现在美国东部时间下午3点左右,当时加密货币交易所币安的推特账户在推特上发布了一条消息表示已与“CryptoForHealth”合作,向社区返还5000枚比特币,并提供人们可以捐款或汇款的链接。
Minutes after that, similar tweets went out from the accounts of other cryptocurrency exchanges, and from the Twitter accounts for democratic presidential candidate Joe Biden, Amazon CEO Jeff Bezos, President Barack Obama, Tesla CEO Elon Musk, former New York Mayor Michael Bloomberg and investment mogul Warren Buffett.
几分钟后,其他加密货币交易所的账户以及民主党总统候选人乔·拜登、Amazon 首席执行官杰夫·贝佐斯、总统贝拉克·奥巴马、特斯拉首席执行官埃隆·马斯克、前纽约市长迈克尔·布隆伯格和投资大亨沃伦·巴菲特的推特账户也发出了类似的推文。
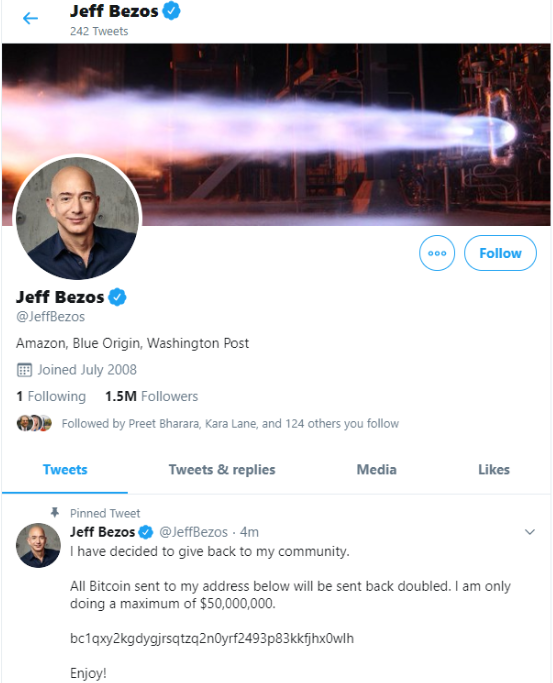
While it may sound ridiculous that anyone would be fooled into sending bitcoin in response to these tweets, an analysis of the BTC wallet promoted by many of the hacked Twitter profiles shows that over the past 24 hours the account has processed 383 transactions and received almost 13 bitcoin — or approximately USD $117,000.
虽然任何人都会被愚弄发送比特币来回应这些推文,这听起来可能很荒谬,但对比特币钱包的分析,许多被黑客入侵的推特个人资料所推广的数据显示,在过去24小时内,该账户处理了383笔交易,收到了近13枚比特币,约合117000美元。
Twitter issued a statement saying it detected “a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools. We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.”
推特发表声明称其检测到“有人通过访问内部系统和工具成功地针对我们的一些员工进行了协调的社会工程攻击。我们知道他们利用这种访问控制了许多高度可见的(包括已验证的)账户和代表他们的推特。我们正在调查他们可能进行了哪些其他恶意活动或访问了哪些信息,并将在这里分享更多信息。”
There are strong indications that this attack was perpetrated by individuals who’ve traditionally specialized in hijacking social media accounts via “SIM swapping,” an increasingly rampant form of crime that involves bribing, hacking or coercing employees at mobile phone and social media companies into providing access to a target’s account.
有强有力的迹象表明,这次攻击是专门通过 “SIM交换” 劫持社交媒体账户的,这是一种越来越猖獗的犯罪形式,涉及贿赂、黑客攻击或胁迫手机和社交媒体公司的员工访问目标的账户。
People within the SIM swapping community are obsessed with hijacking so-called “OG” social media accounts. Short for “original gangster,” OG accounts typically are those with short profile names (such as @B or @joe). Possession of these OG accounts confers a measure of status and perceived influence and wealth in SIM swapping circles, as such accounts can often fetch thousands of dollars when resold in the underground.
SIM卡交换社区 中的人们痴迷于劫持所谓的“OG”社交媒体账户。OG 账户是“原始黑帮”的缩写,通常是那些名字简短的账户(如@B或@joe)。拥有这些 OG 账户可以衡量 SIM卡交换圈 中的地位、影响力和财富,因为这些账户在地下转售时往往能卖到数千美元。
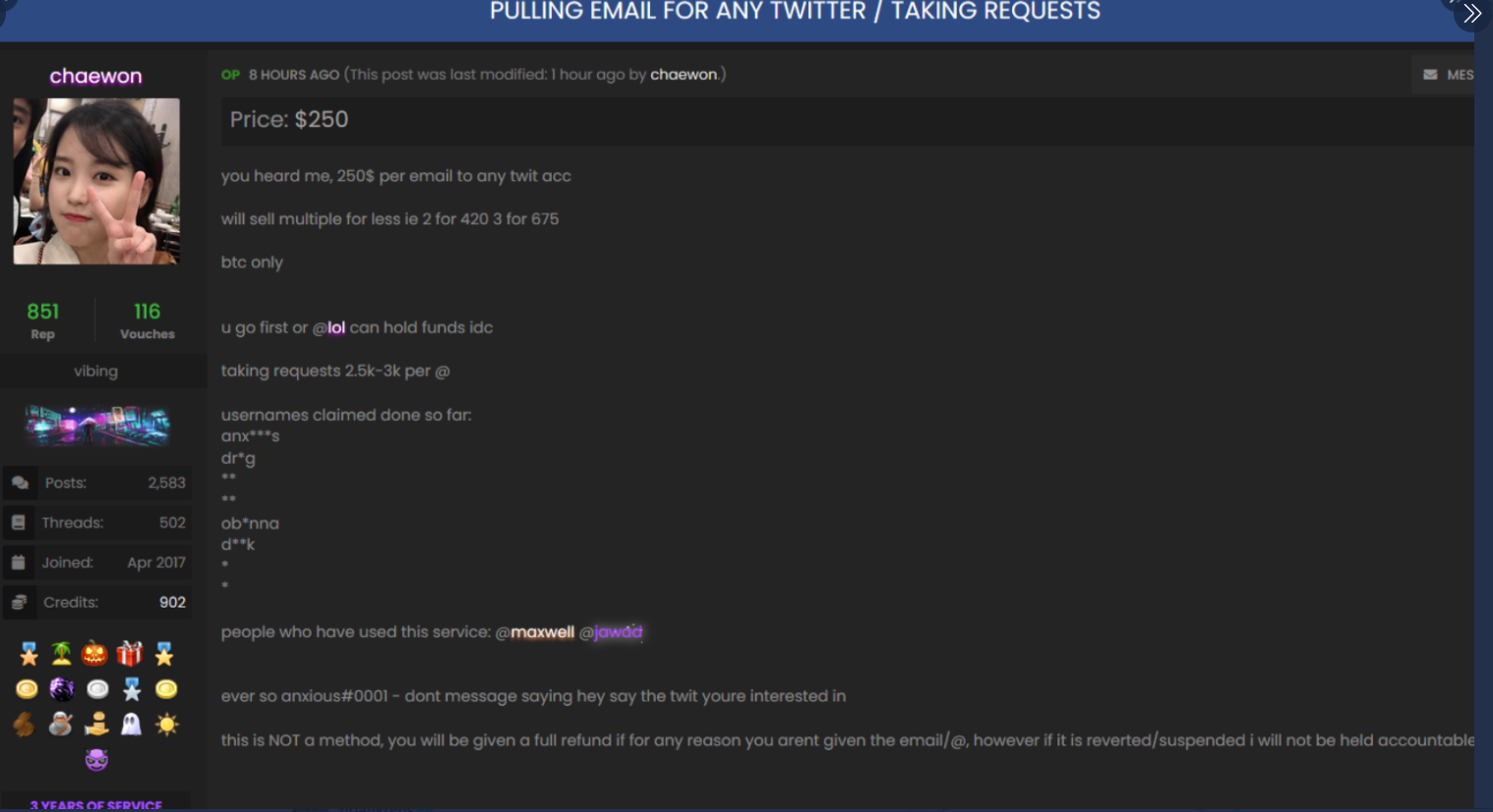
In the days leading up to Wednesday’s attack on Twitter, there were signs that some actors in the SIM swapping community were selling the ability to change an email address tied to any Twitter account. In a post on OGusers — a forum dedicated to account hijacking — a user named “Chaewon” advertised they could change email address tied to any Twitter account for $250, and provide direct access to accounts for between $2,000 and $3,000 apiece.
在周三推特遭到攻击之前的几天里,有迹象表明,SIM卡交换社区中的一些参与者正在出售更改与任何推特账户相关的电子邮件地址的能力。在OGusers上的一篇帖子中——一个专门讨论账户劫持的论坛——一位名为“Chaewon”的用户发布广告称,他们可以以250美元的价格更改与any推特账户相关的电子邮件地址,并提供每个账户 2000 至 3000 美元的直接访问权限。
^ The OGUsers forum user “Chaewon” taking requests to modify the email address tied to any twitter account.
^ OGUsers 论坛用户“Chaewon”接受修改与任何推特账户相关的电子邮件地址的请求。
“This is NOT a method, you will be given a full refund if for any reason you aren’t given the email/@, however if it is revered/suspended I will not be held accountable,” Chaewon wrote in their sales thread, which was titled “Pulling email for any Twitter/Taking Requests.”
Chaewon 在他的销售帖子中写道:“这不是一种方法,如果出于一些原因你没有收到邮件/@,你将得到全额退款。但如果它被尊重/暂停,我将不会被追究责任。”该帖子的标题为“为 任何推特/接受请求 拉取电子邮件。” (译者注:)
Hours before any of the Twitter accounts for cryptocurrency platforms or public figures began blasting out bitcoin scams on Wednesday, the attackers appear to have focused their attention on hijacking a handful of OG accounts, including “@6”。
周三,在加密货币平台的推特账户或公众人物开始引爆比特币骗局的几个小时前,攻击者似乎已经将注意力集中在劫持少数OG账户上,包括“@6”。
That Twitter account was formerly owned by Adrian Lamo — the now-deceased “homeless hacker” perhaps best known for breaking into the New York Times’s network and for reporting Chelsea Manning‘s theft of classified documents. @6 is now controlled by Lamo’s longtime friend, a security researcher and phone phreaker who asked to be identified in this story only by his Twitter nickname, “Lucky225.”
该推特账户以前为[Arian Lamo]所有(krebsonsecurity.com/2018/03/adrian-lamo-hom..)——这位现已去世的“无家可归的黑客”最出名的 Hack 事件是闯入《纽约时报》的网络并被报道是(en.wikipedia.org/wiki/Chelsea_Manning)盗窃机密文件。 @6现在由拉莫的老朋友控制,他是一名安全研究员和电话窃听者他要求在这个故事中只透露他的推特昵称“Lucky225“
Lucky225 said that just before 2 p.m. EDT on Wednesday, he received a password reset confirmation code via Google Voice for the @6 Twitter account. Lucky said he’d previously disabled SMS notifications as a means of receiving multi-factor codes from Twitter, opting instead to have one-time codes generated by a mobile authentication app.
Lucky225 表示,就在美国东部时间周三下午2点之前,他通过 Google Voice收到了 @6 推特账户的密码重置确认码。Lucky 表示,他之前曾禁用短信通知作为从推特接收多因素代码的一种方式,而是选择由移动身份验证应用程序生成一次性代码。
But because the attackers were able to change the email address tied to the @6 account and disable multi-factor authentication, the one-time authentication code was sent to both his Google Voice account and to the new email address added by the attackers.
但由于攻击者能够更改与 @6 帐户绑定的电子邮件地址并禁用多因素身份验证,因此一次性身份验证代码将被发送到他(译者注:指 @6)的谷歌语音帐户和攻击者添加的新电子邮件地址。
“The way the attack worked was that within Twitter’s admin tools, apparently you can update the email address of any Twitter user, and it does this without sending any kind of notification to the user,” Lucky told KrebsOnSecurity. “So [the attackers] could avoid detection by updating the email address on the account first, and then turning off 2FA.”
Lucky 告诉 KrebsOnSecurity:“攻击的方式是,在推特的管理工具中,显然你可以更新任何推特用户的电子邮件地址,而且它不会向用户发送任何通知。”。“因此,[攻击者]可以通过首先更新帐户上的电子邮件地址,然后关闭2FA来避免检测。”
Lucky said he hasn’t been able to review whether any tweets were sent from his account during the time it was hijacked because he still doesn’t have access to it (he has put together a breakdown of the entire episode at this Medium post).
Lucky 说,他无法查看在他的账户被劫持期间是否有推文被发送,因为他仍然无法访问(他已经整理了整个事件的详细信息在本Medium帖子中: medium.com/@lucky225/the-twitter-hack-what-..)。
But around the same time @6 was hijacked, another OG account – @B — was swiped. Someone then began tweeting out pictures of Twitter’s internal tools panel showing the @B account.
但大约在@6被劫持的同时,另一个 OG 账户——@B——也被刷了。然后有人开始在推特上发布推特内部工具面板显示 @B 账户的图片。
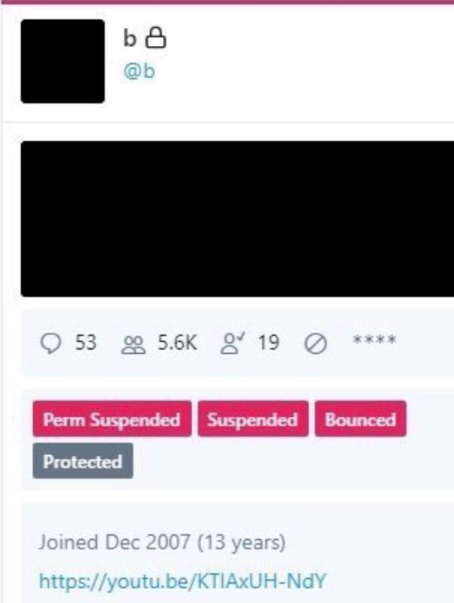
A screenshot of the hijacked OG Twitter account “@B,” shows the hijackers logged in to Twitter’s internal account tools interface.
被劫持的OG推特账户“@B”的截图显示,劫持者登录了推特的内部账户工具界面。
Twitter responded by removing any tweets across its platform that included screenshots of its internal tools, and in some cases temporarily suspended the ability of those accounts to tweet further.
作为回应,推特删除了其平台上任何包含其内部工具截图的推文,并在某些情况下暂时暂停了这些账户进一步推文的能力。
Another Twitter account — @shinji — also was tweeting out screenshots of Twitter’s internal tools. Minutes before Twitter terminated the @shinji account, it was seen publishing a tweet saying “follow @6,” referring to the account hijacked from Lucky225.
^ The account “@shinji” tweeting a screenshot of Twitter’s internal tools interface.
^ 账号“@shinji”在推特上发布了推特内部工具界面的截图。
Cached copies of @Shinji’s tweets prior to Wednesday’s attack on Twitter are available here and here. Those caches show Shinji claims ownership of two OG accounts on Instagram — “j0e” and “dead.”
KrebsOnSecurity heard from a source who works in security at one of the largest U.S.-based mobile carriers, who said the “j0e” and “dead” Instagram accounts are tied to a notorious SIM swapper who goes by the nickname “PlugWalkJoe.” Investigators have been tracking PlugWalkJoe because he is thought to have been involved in multiple SIM swapping attacks over the years that preceded high-dollar bitcoin heists.
KrebsOnSecurity 从一位在美国最大的移动运营商之一从事安全工作的消息人士那里获悉,该消息人士表示,“j0e”和“dead”的 Instagram 账户与一名臭名昭著的 SIM卡交换者 有关,此人绰号“PlugWalkJoe”。“调查人员一直在追踪 PlugWalkJoe,因为据信他在高美元比特币抢劫案之前的几年里参与了多起 SIM卡交换攻击。
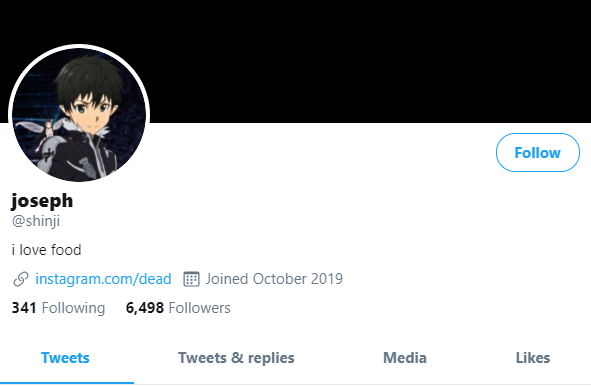
Archived copies of the @Shinji account on twitter shows one of Joe’s OG Instagram accounts, “Dead.”
推特上 @Shinji 账号的存档副本显示了 Joe 的一个 OG Instagram账号“Dead”
Now look at the profile image in the other Archive.org index of the @shinji Twitter account (pictured below). It is the same image as the one included in the @Shinji screenshot above from Wednesday in which Joseph/@Shinji was tweeting out pictures of Twitter’s internal tools.
现在看看 @Shinji 推特账户的另一个 Archive.org 索引中的个人资料图片(如下图所示)。这张图片与周三的 @Shinji 截图中的图片相同,Joseph/@Shinji 在推特上发布了推特内部工具的图片。
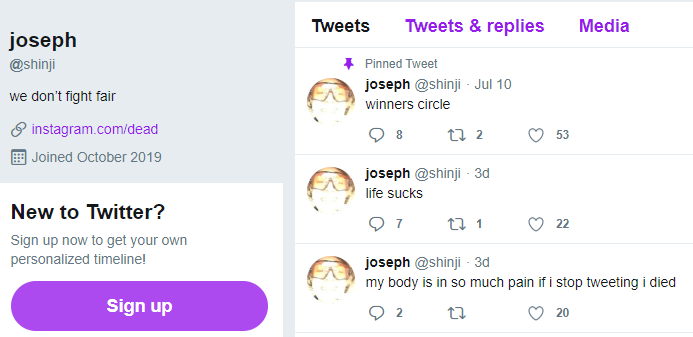
Image: Archive.org 图源:Archive.org
This individual, the source said, was a key participant in a group of SIM swappers that adopted the nickname “ChucklingSquad,” and was thought to be behind the hijacking of Twitter CEO Jack Dorsey‘s Twitter account last year. As Wired.com recounted, @jack was hijacked after the attackers conducted a SIM swap attack against AT&T, the mobile provider for the phone number tied to Dorsey’s Twitter account.
消息人士称,此人是一组 SIM卡交换者 的关键参与者,该交换者昵称为“*ChucklingSquad”,被认为是去年劫持推特首席执行官Jack Dorsey推特账户的幕后黑手。正如Wired.com 报道,在攻击者对 AT&T 进行SIM卡交换攻击后,@jack 被劫持。AT&T 是多西推特账户上电话号码的移动提供商。 (译者注:AT&T 一般指美国国际电话电报公司。美国电话电报公司是一家美国电信公司,创建于1877年,曾长期垄断美国长途和本地电话市场。 AT&T 总部位于得克萨斯州圣安东尼奥。)
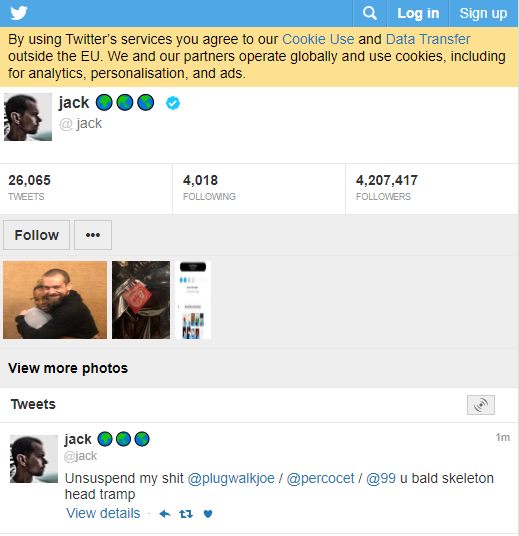
A tweet sent out from Twitter CEO Jack Dorsey’s account while it was hijacked shouted out to PlugWalkJoe and other Chuckling Squad members.
推特首席执行 官杰克·多尔西 的账户被劫持时发出的一条推文向 PlugWalkJoe 和其他 Chuckling Squad 成员喊话。
The mobile industry security source told KrebsOnSecurity that PlugWalkJoe in real life is a 21-year-old from Liverpool, U.K. named Joseph James O’Connor. The source said PlugWalkJoe is in Spain where he was attending a university until earlier this year. He added that PlugWalkJoe has been unable to return home on account of travel restrictions due to the COVID-19 pandemic.
移动行业安全消息人士告诉 KrebsOnSecurity,现实生活中的 PlugWalkJoe 是一位来自英国利物浦的21岁男子,名叫Joseph James O'Connor。消息人士说,PlugWalkJoe 在西班牙,直到今年早些时候他还在那里上大学。他补充说,由于新冠肺炎疫情造成的旅行限制,PlugWalkJoe无法回家。
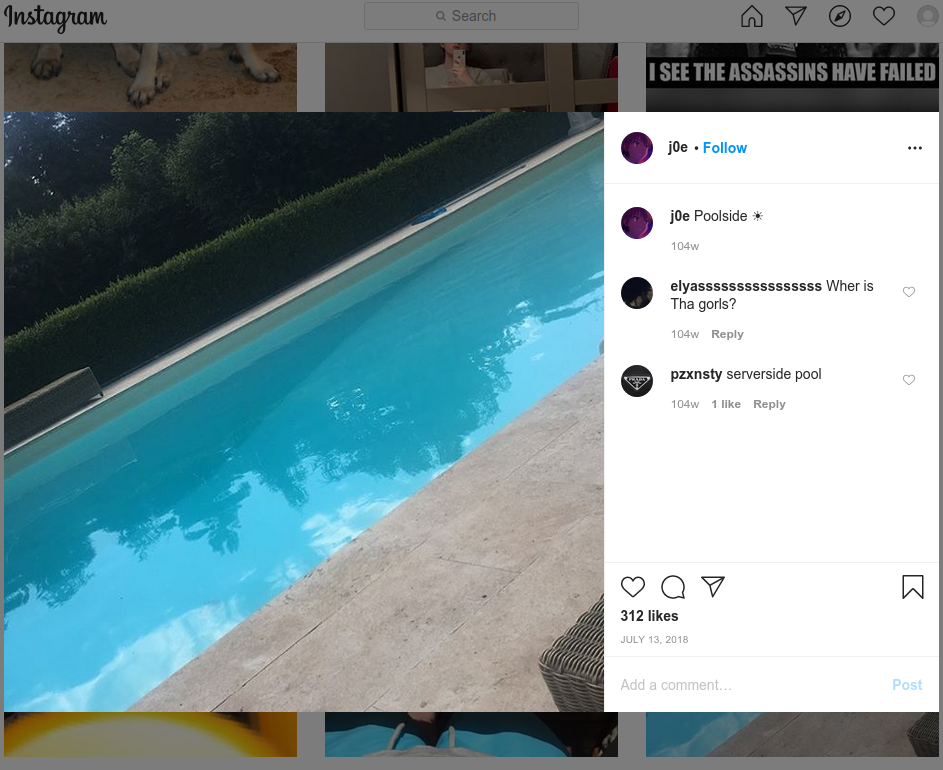
The mobile industry source said PlugWalkJoe was the subject of an investigation in which a female investigator was hired to strike up a conversation with PlugWalkJoe and convince him to agree to a video chat. The source further explained that a video which they recorded of that chat showed a distinctive swimming pool in the background.
移动行业消息人士表示,PlugWalkJoe 是一项调查的对象,在该调查中,一名女性调查员被雇佣与 PlugWalkJoe 进行对话,并说服他同意视频聊天。消息人士进一步解释说,他们录制的聊天视频显示,背景中有一个独特的游泳池。
According to that same source, the pool pictured on PlugWalkJoe’s Instagram account (instagram.com/j0e) is the same one they saw in their video chat with him.
根据同一消息来源,PlugWalkJoe 的Instagram账户上的游泳池与他们在与他的视频聊天中看到的游泳池是同一个。
If PlugWalkJoe was in fact pivotal to this Twitter compromise, it’s perhaps fitting that he was identified in part via social engineering. Maybe we should all be grateful the perpetrators of this attack on Twitter did not set their sights on more ambitious aims, such as disrupting an election or the stock market, or attempting to start a war by issuing false, inflammatory tweets from world leaders.
如果 PlugWalkJoe 真的是推特妥协的关键,那么他在一定程度上是通过社会工程被识别出来的,这也许是合适的。也许我们都应该感谢推特上这次袭击的肇事者没有将目光投向更雄心勃勃的目标,比如破坏选举或股市,或者试图通过发布世界领导人的虚假煽动性推文来发动战争。
Also, it seems clear that this Twitter hack could have let the attackers view the direct messages of anyone on Twitter, information that is difficult to put a price on but which nevertheless would be of great interest to a variety of parties, from nation states to corporate spies and blackmailers.
此外,很明显,这次推特黑客攻击可能会让攻击者查看推特上任何人的直接信息,这些信息很难定价,但从民族国家到企业间谍和勒索者,各方都会对此感兴趣。
This is a fast-moving story. There were multiple people involved in the Twitter heist. Please stay tuned for further updates.
这是一个快速发展的故事。有多人参与了Twitter抢劫案。感谢221B Unit,他们在连接这个故事中的一些方面提供的帮助。
This entry was posted on Thursday 16th of July 2020 05:41 PM